Protect and secure your electronic communications with a complete, cloud-based security and compliance solution. Powerful enterprise class Email Security, Social Media Protection, Continuity and Archiving tools protect from advanced threats, compliance risk and digital fraud.
Email Threat Protection, powered by Proofpoint, provides a comprehensive set of tools to stop inbound and outbound Email threats before they can cause harm. Leverage this powerful cloud-based platform to enhance your security and compliance posture.
BENEFITS
- Enterprise class threat protection powered by Proofpoint
- Protects critical Email resources, both on-premises and in the cloud
- High availability cloud platform
- Email Security tools stop threats before they reach your network
- Email Continuity ensures mail can flow even when the primary service is offline
- Email Archiving preserves all emails and attachments for compliance
- Self-service portal allows each end user to manage their personal settings
- No customer hardware required
BUNDLES
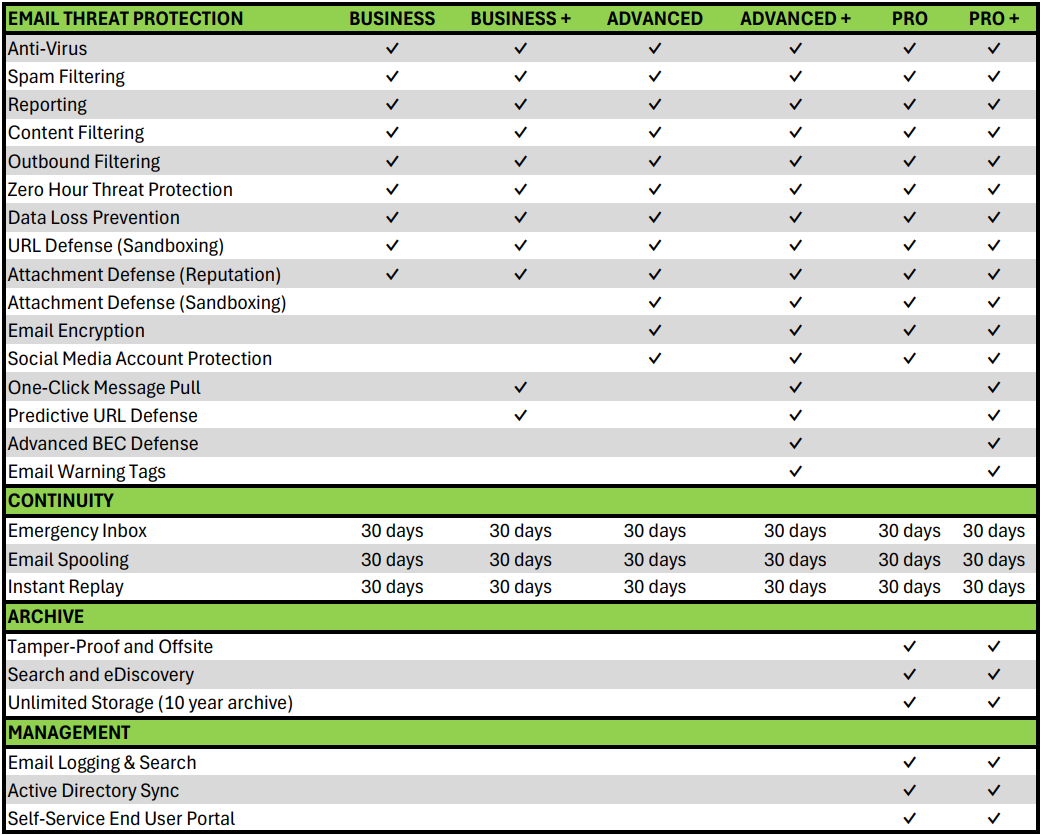
Email Threat Protection, fully compatible with on-premises Exchange or Microsoft 365 is available through three bundles designed to meet both security and budget requirements.
All bundles offer predictable monthly pricing based on mailbox count.
- BUSINESS – Email Security tools that every organization needs
- ADVANCED – Adds Email Encryption & Social Media Protection
- PROFESSIONAL – Adds Email Archiving
- BUSINESS + – Adds One-Click Message Pull and Predictive URL Defense
- ADVANCED + – Adds Advanced BEC Defense and Email Warning Tags
- PROFESSIONAL + – Adds Advanced BEC Defense and Email Warning Tags
- No onsite hardware is required to implement Email Threat Protection services.
- Xamin provides an easy to understand Per-User pricing model
- An Onboarding project is required.
- Xamin will provide firewall configuration information, including IP addresses, port rules and DNS configuration information needed to facilitate communication.
SECURITY
FEATURE & BENEFITS GUIDE
Anti-Virus
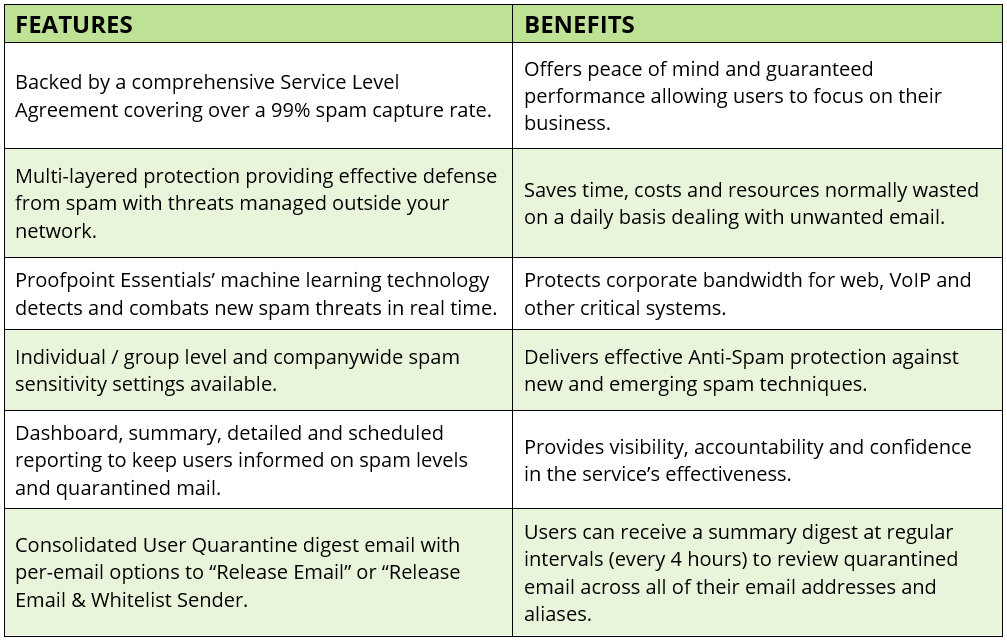
Email Threat Protection, powered by Proofpoint's threat detection technology provides customers with unrivalled protection from viruses, malware and other Email-borne threats. The sophisticated anti-virus engines operate at the highest levels of accuracy, performance, and effectiveness, blocking all known viruses. Heuristic scanning additionally discovers and protects against currently unknown viruses for added security and reassurance.

SPAM Filtering
Powered by the patented Proofpoint MLX machine learning technology, SPAM and phishing technology efficiently filters millions of possible attributes in every email. This advanced level scanning protection accurately filters emails by examining envelope headers, structure, content, sender reputation, images and more. Prevent SPAM, malware, malicious email and attachment-based threats.
Reporting
Flexible online reporting dashboards and detailed email reporting available with one click for insightful management control.

Outbound Filtering
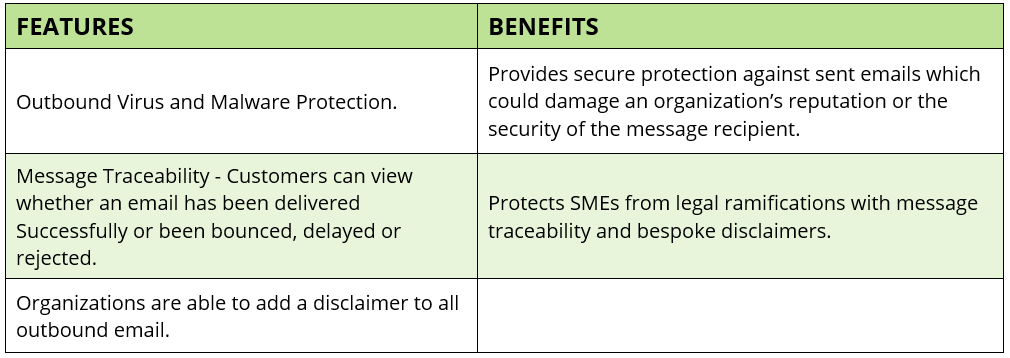
Outbound filtering ensures all email sent via the Proofpoint platform is free from viruses, malware and other malicious content.
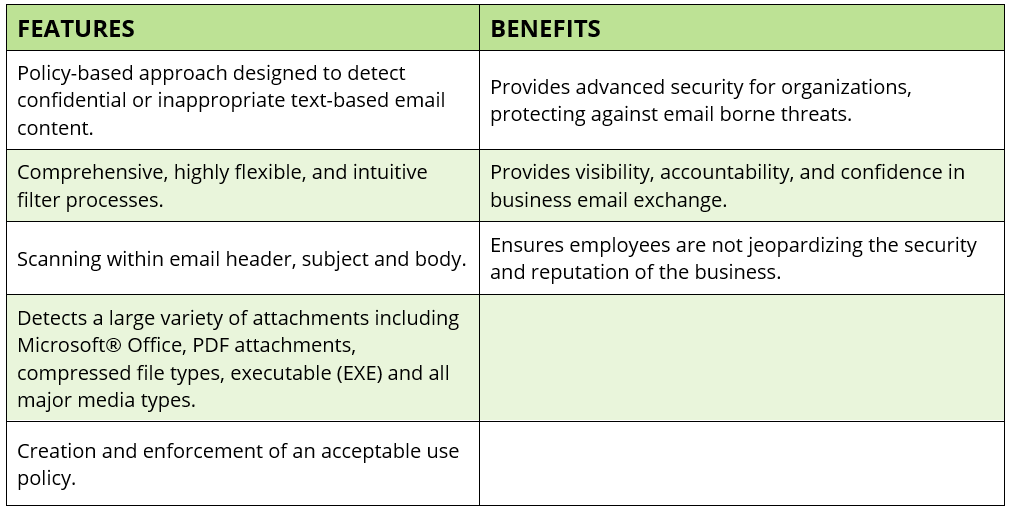
Content Filtering
Proofpoint's intelligent email Content Filter service enables organizations to use a flexible rules engine to enforce email communication policies.
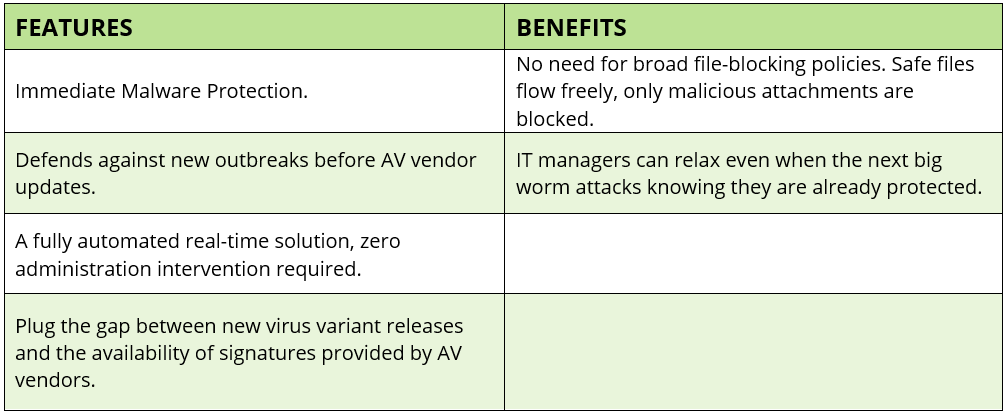
Zero Hour Outbreak
This feature instantly protects users against new, unknown email threats as soon as they arise, so you know that your inbox is always secure.
URL Defense
Leveraging the advanced power of Targeted Attack Protection, Proofpoint’s Industry Leading email analysis solution, to provide small to midsized enterprises with URL Defense, the only service that effectively detects, catches and analyses malicious URLs.
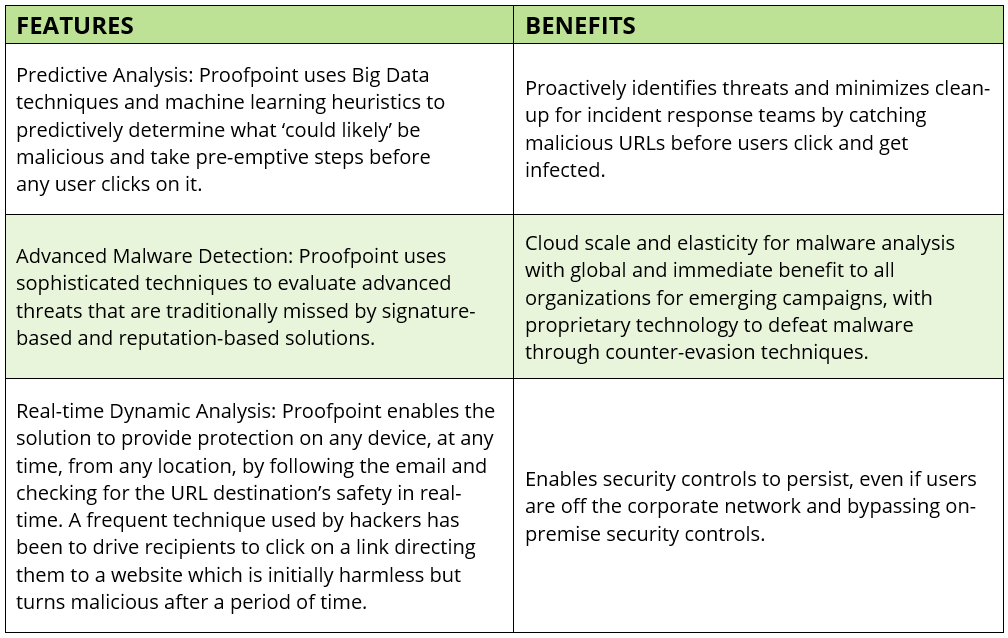
Attachment Defense
Leveraging the advanced power of Targeted Attack Protection, Proofpoint’s Industry Leading email analysis solution, to provide small to midsized enterprises with Attachment Defense to effectively detect malicious attachments.

Data Loss Protection
Block Data Loss and Comply with Regulatory Policies.

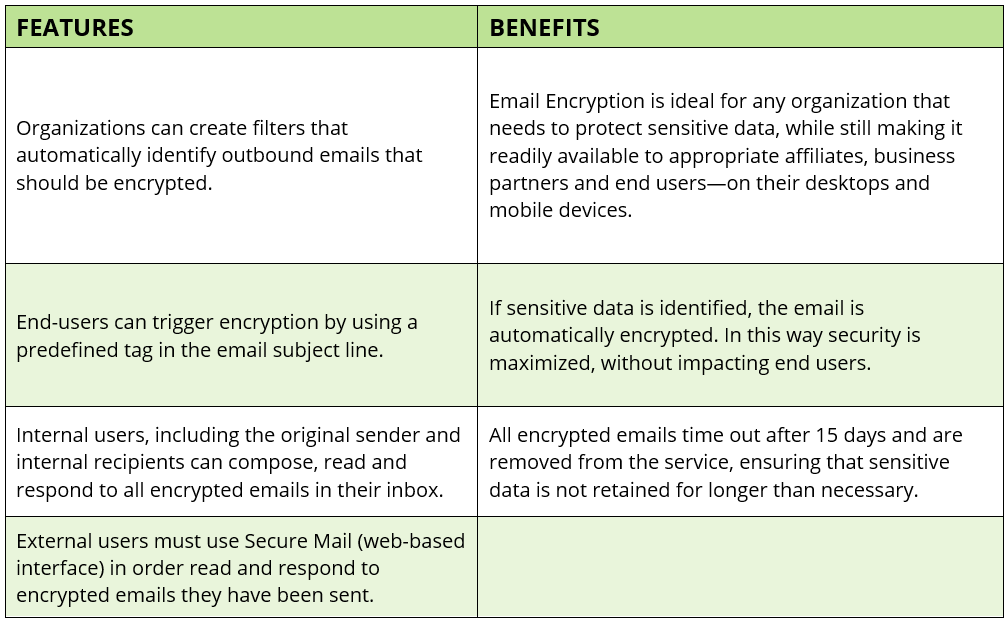
Email Encryption
Purpose built to help small and medium enterprises reduce the potential negative impacts of data loss by automatically encrypting email.
Social Media Account Protection
Advanced Protection for your Social Media Accounts.

Advanced BEC Defense
Identifies and stops hard to detect business email compromise (BEC) and social engineering attacks common in payment redirect scams, supplier invoicing fraud, and targeted phishing campaigns. Proofpoint observed 3X detection improvement for BEC in preliminary testing.
These types of threats require a more sophisticated detection technique since there’s often no malicious payload to detect. Advanced BEC Defense is powered by Supernova, our latest behavioral AI engine, which analyzes multiple message attributes such as message header data, sender IP address and message body for sentiment analysis.
Email Warning Tags
Reduce risk by making customers more aware and cautious of potentially dangerous messages. The Email Warning Tag feature automatically identifies suspicious messages and inserts banners into the message body, offering a short description of the risk associated with that email.
These tags are customizable, mobile responsive, and easily understandable for users. Knowing more about where and who an email is coming from helps them make better in-the-moment security decisions.
Predictive URL Defense
Keeps users protected by discovering malicious URLs used in phishing campaigns and advanced ransomware attacks more quickly. Predictive URL Defense runs continuously, automatically sandboxing suspicious links based on smart triggers and email traffic patterns.
This added layer of defense blocks compromised messages before they land in a user’s inbox. No human interaction needed.
One-Click Message Pull
Improves time to message remediation for administrators controlling mail flow in Microsoft 365 accounts. This feature gives admins an easy path through Email Logs to remove or restore a delivered message with a single click. This drastically improves efficiency and time spent on mail management.
CONTINUITY
FEATURE & BENEFITS GUIDE
Emergency Inbox
The emergency inbox gives automatic access to your email if your server fails or unexpected downtime.

Instant Replay
With the Proofpoint Instant Replay feature, end users can easily replay successfully delivered emails received in the last 30 days, which may have been wrongly deleted or accidentally removed from servers.
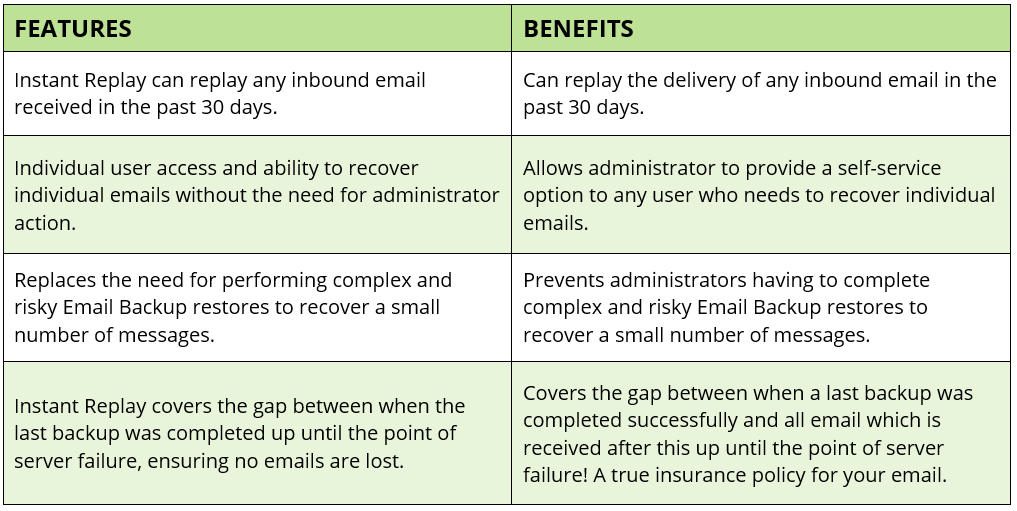
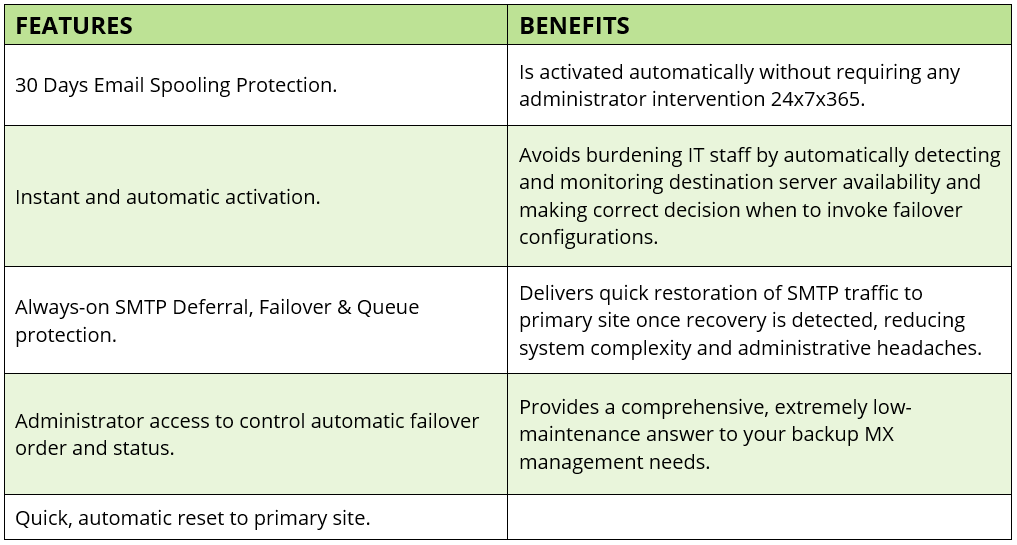
Email Spooling
Email Spooling and Failover provides a comprehensive, extremely low-maintenance answer to your backup MX management needs. It preserves email metadata during an outage and delivers quick restoration of SMTP traffic to the primary site once recovery is detected.
ARCHIVING
FEATURE & BENEFITS GUIDE
Unlimited E-mail Archive (10 year)
Eliminate data storage constraints and meet legal and regulatory obligations with Proofpoint 10-year cloud archive, which ensures that you stay protected and compliant.


Search & e-Discovery
The Proofpoint email archive comes with advance search capabilities for super-fast and easy retrieval of a specific email or attachment.

MANAGEMENT
FEATURE & BENEFITS GUIDE
Email Logging & Search
Email logs contain the email history of a user for a 30-day period. Users can quickly and easily search the email logs for both inbound & outbound filtered email including that of alias addresses imported from active directory or added manually.

Active Directory Sync
Active directory keeps all your functional users’ information up to date by automatically syncing with the platform once every 24 hours.

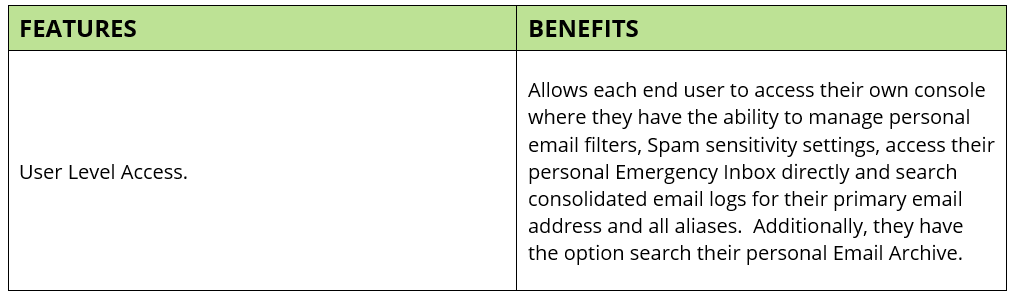
Self-Service End User Portal
The Proofpoint user interface has been built to service the management needs of all user types, allowing end users the access to manage their own personal account settings.
Service Overview
SCOPE OF SERVICES:
Email Threat Protection
INCIDENT RESPONSE
DURING BUSINESS HOURS SUPPORT:
- 1.Xamin will provide live Technical Support during Business Hours for service requests related to the Email Threat Protection platform:
- a.Client Submitted Requests:
- 1.Support requests can be submitted during posted Business Hours via:
- Desk Director
- Phone
- 2.An Xamin support technician will triage the Support Ticket and will provide a response based on the agreement SLA.
- 3.The support technician will troubleshoot and resolve the issue directly with the end user that requested the service.
- 1.Support requests can be submitted during posted Business Hours via:
- a.Client Submitted Requests:
INCIDENT RESPONSE
AFTER HOURS SUPPORT:
- 1.Xamin will provide Emergency support for service requests related to the Email Threat Protection platform.
- 2.Requests can be submitted via Phone only to our Emergency support line.
- a.Emergency support is limited to the following requests:
- Platform Availability
- Email delivery issues affecting the entire organization
- All other requests will be addressed at the beginning of the next business day.
- a.Emergency support is limited to the following requests:
OUT OF SCOPE OF SERVICES:
HOURLY SUPPORT:
- 1.Support for the following items will be charged on an hourly basis. Xamin will seek approval prior to commencing work.
- 2.Hourly fees are billed in 1 minute increments.
- 3.Hourly support items include, but are not limited to:
- Technical support for client Email systems (Exchange or Microsoft 365).
- Technical Support for DNS mail records, including MX, DMARC, SPF & DKIM.
- Assistance in setup or troubleshooting of Email applications (i.e. Microsoft Outlook).
- Assistance in setup or troubleshooting of Mobile Devices to receive Email (i.e. iPhone, Android).
- Troubleshooting of any Email issues not directly related to the platform.
- Setup or troubleshooting of Email domain issues (i.e. examplecorp.com).
- Requests for non-emergency work to be completed after Business Hours
- Onsite Support.
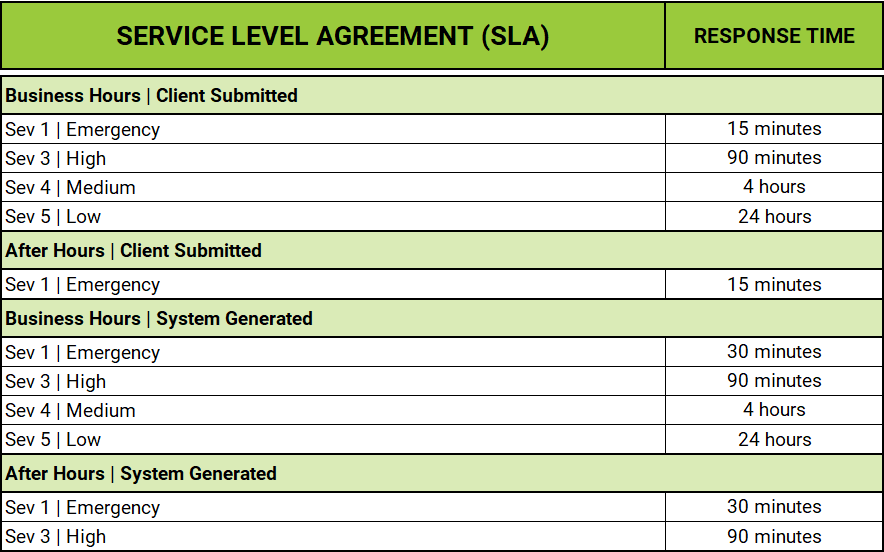
SERVICE LEVEL AGREEMENT
TECHNICAL SUPPORT HOURS:
Xamin Technical Support Hours:
- a.Business Hours: 8:00 AM – 5:00 PM CST Monday – Friday.
- b.Emergency support is provided outside of normal business hours.
- c.Holidays and office closures are determined on an annual basis and are available on our home page at www.xamin.coms://www.xamin.com
RESPONSE TIME