SERVICE DETAILS
Quickly detect, respond, and harden your security posture against modern cyberattacks. Our Detection & Response service, powered by Fortra's Alert Logic, leverages a cloud-first security platform backed by 24/7 expertise to hunt down advanced cyberthreats, perform forensics and mitigate impact.
Detection & Response, powered by Alert Logic (Fortra) provides comprehensive visibility into your entire security posture through its cloud-based, purpose-built, fully monitored platform.
BENEFITS
- Protect critical resources, both on-premises and in the cloud
- 24/7 ‘eyes on glass’ monitoring by Security Operations (SOC) team
- Identified threats are evaluated and include remediation recommendations
- Robust Client Portal with detailed reporting and log search capabilities
PROTECTION BUNDLES
We offer two security bundles to maximize the protection of your environment, both on-premises and in the Cloud:
- MDR ESSENTIALS – Vulnerability Scanning (Internal & External)
- MDR PROFESSIONAL – Vulnerability Scanning + 24×7 monitoring & alerting by the Security Operations Center (SOC)
- XDR – Vulnerability Scanning + 24×7 monitoring & alerting by the Security Operations Center (SOC) + 3rd party EDR Support with Network & Identity Response

- No client provided hardware required, Xamin provides options for a fully managed Physical or Virtual appliance.
- All bundles offer predicable monthly pricing based on users, servers and devices.
- An Onboarding project is required.
- Xamin will provide firewall configuration information, including IP addresses, port rules and DNS configuration information needed to facilitate communication.
CLOUD-FIRST SECURITY
Detection & Response, powered by Alert Logic is a purpose-built Cloud security platform technology. Our team of security experts work closely with you to understand your unique needs and business context, empowering you to resolve whatever threats may come.
Knowledge of your risk provides vital context to enable the most appropriate response. Industry data, continuous research and machine-learning from aggregated data of thousands of customers are all leveraged to provide actionable solutions to harden your internal and external security posture. The Detection & Response platform delivers real-time reporting and provides access to information on risk, vulnerabilities, remediation activities, configuration exposures, and compliance status. We enable you to focus on a prioritized order of threats that need further triage, drill down into threats to act on or mitigate exposure and provide intuitive visualization of risk.
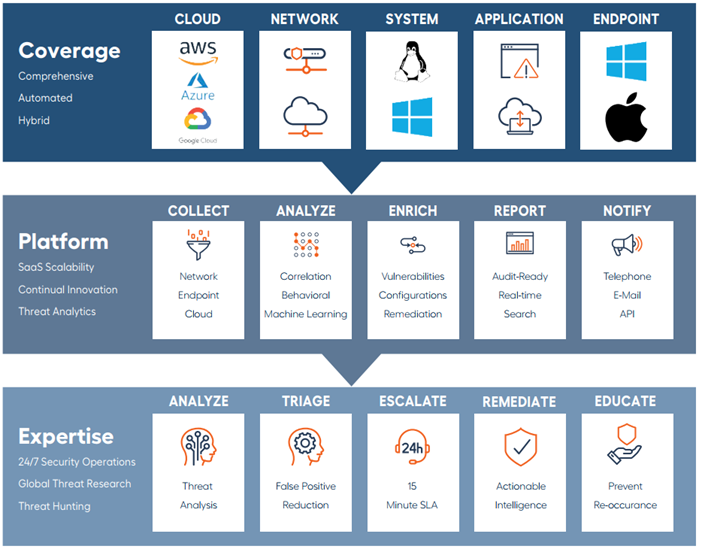
Detection & Response, powered by the Alert Logic monitoring platform, analyzes network traffic and more than 60 billion log messages each day, providing coverage across your entire attack surface and bringing together asset visibility and security analytics for cloud, networks, applications, and endpoints in on-premises, hybrid, and cloud environments.
ESSENTIALS BUNDLE
Vulnerability Scanning of both internal and external resources enables you to discover, benchmark and harden your environment against cyberthreats with regularly scheduled internal and external scans of critical infrastructure. Scheduled quarterly business review (QBR) meetings with the Client Experience Team help to analyze and reinforce your security posture.
PROTECT
RISK MONITORING: Scan for vulnerabilities, misconfigurations and exposure across critical endpoints, networks, and cloud environments.
RISK PRIORITIZATION: Recommendations are enriched with digital risk information to add greater context, quantify your exposure, and to prioritize actions.
ASSET DISCOVERY: Map, profile, and classify assets on your network to help you understand and protect your attack surface.
BENCHMARK
HARDENING: Reveal configuration errors and hardening drift against known benchmarks.
RISK SCORING: Prioritized view of digital risks that exist in your environment, weighted based on severity and benchmarked against industry peers.
ANALYSIS: Automated and exportable risk score trends, action lists, executive summary and risk assessment reports.
HARDEN
REMEDIATE: Resolve identified critical and high vulnerabilities, validate and verify that the vulnerabilities have been successfully addressed.
REPORTING: Create automated and ad-hoc reports with rich charts and dashboards for compliance and executive reporting to elevate visibility and close gaps.
PROFESSIONAL BUNDLE
Professional combines all the features of Detection & Response Essentials, adding Event Log Monitoring, Log Retention and Search. Professional provides 24×7 ‘eyes on glass’ monitoring of perimeter devices, networks and endpoints to detect, respond and harden your environment against modern cyberattacks.
PROTECT
VISIBILITY: Discover and collect security events across your existing technology stack to profile assets and monitor security logs from multiple sources.
24x7 MONITORING: Monitor both internal and IaaS environments around the clock for threats and risks, allowing you to focus on other important areas of your business.
THREAT HUNTING: Analyze and catch threats across all diverse security logs.
RESPOND
INVESTIGATION: Analysis of detected threat activity, minimizing time wasted on false positives.
RETAIN & SEARCH: Encrypted security logs are archived for 12 months by default with robust search capabilities for routine review and security event forensics.
INCIDENT RESPONSE: Detect and respond to critical security incidents to prevent and contain the spread of advanced cyberthreats.
RECOVER
REMEDIATION: We work directly with your team for remediation tasks and strategy recommendations.
ROOT CAUSE: Investigation into the root cause of incidents to harden your posture.
INTELLIGENCE: Security event observations and recommendations are enriched with threat feed data, global threat research and threat hunting to provide granularity and context.
XDR BUNDLE
XDR combines the advanced capabilities of detection and response with expanded visibility, deeper threat intelligence, and seamless integration across endpoints, networks, and clouds. This solution elevates your cybersecurity operations with 24×7 managed detection, automated responses, and enriched insights for effective threat containment and prevention.
PROTECT
COMPREHENSIVE COVERAGE: Unify telemetry from endpoints, networks, cloud environments, and third-party tools for a holistic view of your IT estate.
24x7 MONITORING: Continuous monitoring of all connected systems by a global SOC to detect and neutralize threats before they escalate.
THREAT INTELLIGENCE: Integrate industry-leading threat feeds and the Fortra Threat Brain for enriched detection of known and emerging threats.
USER BEHAVIOR MONITORING: Detect anomalies and risky behavior with advanced user activity profiling.
RESPOND
AUTOMATED ACTIONS: Leverage SOAR capabilities to automate critical response actions, such as endpoint isolation, malicious connection shunning, and credential disabling.
INCIDENT CORRELATION: Centralize analysis by correlating endpoint and network activity for high-confidence threat detection and mitigation.
ON-DEMAND FORENSICS: Quickly retrieve forensic artifacts to analyze incidents and fine-tune detection rules.
MANAGED CONTAINMENT: Enable SOC experts to act on your behalf, containing threats and minimizing impact.
RECOVER
REMEDIATION SUPPORT: Collaborate with your designated SOC team to resolve incidents, validate fixes, and harden defenses.
ROOT CAUSE ANALYSIS: Investigate underlying vulnerabilities to prevent reinfection and strengthen your security posture.
TAILORED CONSULTATION: Access bespoke threat hunting, proactive tuning, and strategic advice to optimize your defenses.
HARDEN
RISK SCORING: Provide a prioritized view of vulnerabilities and risks, contextualized with industry benchmarks.
REAL-TIME REPORTING: Gain access to customizable dashboards and reports, ensuring transparency and compliance for stakeholders.
CLOUD INTEGRATION: Monitor, configure, and secure your cloud infrastructure to reduce misconfigurations and exposure risks.
Service Overview
SERVICE REQUIREMENTS:
Xamin has partnered with Alert Logic to power all Detection & Response services. Alert Logic is an industry leader in Managed Detection & Response services, recognized as a Visionary on the Gartner Magic Quadrant. SECURITY APPLIANCE:
- 1.Detection & Response requires a minimum of one Security Appliance to be deployed in the primary client site, with two flexible deployment options to choose from:
- a.OPTION 1:
- i.Virtual Appliance
- 1.Fully managed, VMware or Hyper-V virtual appliance installed on existing client virtual infrastructure.
- a.Virtual Appliance resource requirements (i.e CPU, Memory, Storage) will vary based on deployment sizing.
- b.https://docs.alertlogic.com/requirements/appliance-requirements.htm
- 2.The Security Appliance must be connected to the primary Core switching network such that it can see all network devices that are to be monitored.
- 1.Fully managed, VMware or Hyper-V virtual appliance installed on existing client virtual infrastructure.
- i.Virtual Appliance
- b.OPTION 2:
- i.Physical Appliance:
- 1.Fully managed, physical hardware appliance.
- a.Client to provide rack or shelving space for the physical hardware.
- b.Physical Appliance requirements will vary based on deployment sizing:
- c.https://docs.alertlogic.com/requirements/appliance-requirements.htm
- 2.The Security Appliance must be connected to the primary Core switching network such that it can see all network devices that are to be monitored.
- 1.Fully managed, physical hardware appliance.
- i.Physical Appliance:
- a.OPTION 1:
FIREWALL RULES:
- 1.Detection & Response services require firewall rules for secure communications to and from the Alert Logic SOC datacenter.
- 2.Current firewall requirements for United States deployments:
OPERATING SYSTEM AND BROWSER REQUIREMENTS:
- 1.The Detection & Response client portal supports the current version and the previous major version of the following Operating Systems and Internet browsers:
SECURITY AGENT REQUIREMENTS:
- 1.The Security Agent requires the following pre-requisites for installation on all Operating Systems to be monitored:
SCOPE OF SERVICES:
Essentials MDR Bundle
SERVICE FEATURES
The Essentials Bundle includes the following features:
- Automated Vulnerability Scanning
- Automated Reporting
- Product Licensing
- Self-service Client Portal access
SERVICE ONBOARDING
- 1.Xamin will conduct an onboarding project with the assistance of Alert Logic security experts to install the service and conduct discovery scans to identify devices and endpoints on the selected networks to be scanned.
- 2.Xamin will work with the Client to identify discovered devices and determine if any device exclusions are necessary based on the Client environment. Devices can be excluded based on IP Address, IP Address range(s) or exclusions of devices on separate vLAN's.
- 3.Once the onboarding is complete:
- a.Automated vulnerability scanning of the environment will commence.
- b.Client will be provided with automated reporting and access to the self-service client portal.
CLIENT PORTAL:
- 1.The Detection & Response Essentials service provides a Client Portal that is available 24/7/365 (excluding planned Maintenance windows).
- 2.The portal provides self-service features and information to enhance the Detection & Response Essentials service experience.
ROBUST REPORTING:
- 1.Automated delivery of detailed reports that outline, rank and classify identified vulnerabilities.
- 2.Detailed threat information is provided in the reports and via the Client Portal
BUSINESS HOURS SUPPORT:
- 1.Xamin will provide live Technical Support during Business Hours for service requests related to the Detection & Response platform. Technical support is provided for troubleshooting of the service features only.
- a.Client Submitted Requests:
- 1.Support requests can be submitted during posted Business Hours via:
- Desk Director
- Phone
- 2.An Xamin support technician will triage the Support Ticket and will provide a response based on the agreement SLA.
- 3.The support technician will troubleshoot and resolve the issue directly with the end user that requested the service.
- 1.Support requests can be submitted during posted Business Hours via:
- a.Client Submitted Requests:
- 1.If remediation of vulnerabilities is desired:
- a.OPTION 1:
- i.Add additional support services to your support Agreement.
- ii.Firewall Management
- 1.Remediation of Critical and High findings related to the firewall infrastructure are included as part of the Agreement fees for Firewall Management.
- iii.Infrastructure Protection + Support
- 1.Remediation of Critical and High findings related to server, storage and network infrastructure are included as part of the Agreement fees for Infrastructure Protection + Support services.
- iv.Remediation of all Medium & Low findings are charged on an hourly basis.
- v.Remediation of all Workstation findings are charged on an hourly basis
- b.OPTION 2:
- i.Remediation services can be provided upon request on an hourly basis if no Support Agreement is in place.
- ii.Requires that Xamin is provided remote access to the affected system(s) for remediation.
- a.OPTION 1:
AFTER HOURS SUPPORT:
- 1.For Clients under a Support Agreement:
- i.Client submitted requests:
- 1.Emergency support is only available for platform availability issues.
- 2.Requests can be submitted via Phone only to our Emergency support line.
- 3.All other requests will be addressed at the beginning of the next business day.
- i.Client submitted requests:
- a.For Clients not under a Support Agreement:
- i.Client submitted requests:
- 1.Xamin does not offer emergency support for clients not under a Support Agreement.
- 2.All requests will be addressed at the beginning of the next business day and billed on an hourly basis.
- i.Client submitted requests:
SCOPE OF SERVICES:
Professional MDR Bundle
SERVICE FEATURES
The Professional Bundle includes the following features:
- The Professional bundle includes all the features of the Essentials Bundle
- 24/7 'eyes on glass' Security Operations Center (SOC)
- 24/7 critical event monitoring, response, triage and client contact
- Product Licensing
- Automated Reporting
- Self-service Client Portal access
- 100MB/day/node storage allocation
- 12 month rolling log retention
SERVICE ONBOARDING
- 1.Xamin will conduct an onboarding project with the assistance of Alert Logic security experts to install the service and conduct discovery scans to identify devices and endpoints on the selected networks to be protected.
- 2.Xamin will work with the Client to identify discovered devices and determine if any device exclusions are necessary based on the Client environment. Devices can be excluded based on IP Address, IP Address range(s) or exclusions of devices on separate vLAN's.
- 3.Xamin will configure devices selected for Event Log Monitoring to ensure logs are securely transferred to Alert Logic for continuous monitoring and analysis.
- a.The Professional bundle includes 100MB/day/node storage allocation.
- b.Log usage not to exceed an aggregated average of 100MB/day/node in any calendar quarter.
- c.Additional charges will be required if log storage exceeds the limits shown above.
- 4.Once the onboarding is complete:
- a.Automated vulnerability scanning of the environment will commence.
- b.Event Logs for onboarded devices will be ingested and monitored 24/7 by the Alert Logic SOC team.
- c.Security threats will be ranked on severity with detailed threat information and remediation recommendations.
- d.Critical threats will be escalated and triaged by the Alert Logic SOC team.
- i.Xamin will be notified 24/7/365 of any escalated threats that are deemed Critical.
- e.Client will be provided with automated reporting and access to the self-service client portal.
- f.Event logs will be securely stored and retained by Alert Logic
- i.All ingested event logs are fully searchable via the self-service client portal.
- ii.The Professional bundle includes an initial 12 months of rolling log retention.
- iii.Longer terms available (up to 7 years) to meet compliance and/or policy requirements.
CLIENT PORTAL
- 1.The Detection & Response Professional service provides a Client Portal that is available 24/7/365 (excluding planned Maintenance windows).
- 2.The portal provides self-service features including fully searchable logs, access to reporting, and information to enhance the the Detection & Response service experience.
ROBUST REPORTING:
- 1.Automated delivery of detailed reports that outline, rank and classify identified vulnerabilities. Detailed information is provided in the reports and via the Client Portal
BUSINESS HOURS SUPPORT:
- 1.Xamin will provide live Technical Support during Business Hours for service requests related to the Detection & Response platform. Technical support is provided for troubleshooting of the service features only.
- a.Client Submitted Requests:
- 1.Support requests can be submitted during posted Business Hours via:
- Desk Director
- Phone
- 1.An Xamin support technician will triage the Support Ticket and will provide a response based on the agreement SLA.
- 2.The support technician will troubleshoot and resolve the issue directly with the end user that requested the service.
- 1.Support requests can be submitted during posted Business Hours via:
- a.Client Submitted Requests:
- 1.If remediation of vulnerabilities or security events is desired:
- a.OPTION 1:
- i.Add additional support services to your support Agreement.
- ii.Firewall Management
- 1.Remediation of Critical and High findings related to the firewall infrastructure are included as part of the Agreement fees for Firewall Management.
- iii.Infrastructure Protection + Support
- 1.Remediation of Critical and High findings related to server, storage and network infrastructure are included as part of the Agreement fees for Infrastructure Protection + Support services.
- iv.Remediation of all Medium & Low findings are charged on an hourly basis.
- v.Remediation of all Workstation findings are charged on an hourly basis
- b.OPTION 2:
- i.Remediation services can be provided upon request on an hourly basis if no Support Agreement is in place.
- ii.Requires that Xamin is provided remote access to the affected system(s) for remediation.
- a.OPTION 1:
AFTER HOURS SUPPORT:
- 1.Critical Security Events:
- a.For Clients under a Support Agreement:
- i.Escalated Security Events:
- 1.Xamin will be notified by the SOC team for escalated Critical events.
- 2.Xamin will notify & the Client via the Emergency Call Tree.
- 3.Xamin will work to troubleshoot and resolve the issue(s).
- ii.Client submitted requests:
- 1.Emergency support is only available for platform availability issues.
- 2.Requests can be submitted via Phone only to our Emergency support line.
- 3.All other requests will be addressed at the beginning of the next business day.
- i.Escalated Security Events:
- b.For Clients not under a Support Agreement:
- i.Escalated Security Events:
- 1.Client will be notified directly by the SOC team for escalated Critical events.
- ii.Client submitted requests:
- 1.Xamin does not offer emergency support for clients not under a Support Agreement.
- 2.All requests will be addressed at the beginning of the next business day and billed on an hourly basis.
- i.Escalated Security Events:
- a.For Clients under a Support Agreement:
OUT OF SCOPE OF SERVICES:
HOURLY SUPPORT:
- 1.Support for the following items will be charged on an hourly basis. Xamin will seek approval prior to commencing work.
- a.Hourly support items include, but are not limited to:
- i.Troubleshooting of security observations ranked as Informative, Low or Medium.
- ii.Requests for non-emergency work to be completed After Hours.
- iii.Customized event correlation.
- iv.Onsite Support.
- v.Hourly fees are billed in 1 minute increments.
- a.Hourly support items include, but are not limited to:
- 2.If the Client has contracted the following services in addition to Detection & Response and hardware/software is included in the Support Catalog, hourly charges may be considered in scope, covered by the Agreement and not subject to hourly charges:
- Firewall Management
- Infrastructure Protection + Support
SCOPE OF SERVICES: XDR BUNDLE
SERVICE FEATURES
The XDR Bundle includes the following features:
- Comprehensive integration of endpoint, network, and cloud security telemetry.
- 24/7 monitoring, detection, and response by a global Security Operations Center (SOC).
- Advanced threat intelligence via Fortra Threat Brain for known and emerging threats.
- Automated responses to critical incidents, including endpoint isolation, credential disablement, and malicious connection blocking.
- Single Fortra (Alert Logic) agent deployment for unified telemetry collection.
- Incident correlation across endpoints, networks, and identity platforms.
- Real-time reporting, dashboards, and insights via a self-service client portal.
- 12-month rolling log retention.
SERVICE ONBOARDING
Xamin will perform an onboarding project in collaboration with Fortra (Alert Logic) security experts, including the following steps:
- 1.Discovery and Configuration:
- Conduct discovery scans to identify devices, endpoints, and cloud resources across the client environment.
- Work with the client to exclude devices based on IP addresses, ranges, or VLAN segregation if required.
- 1.Agent Installation and Configuration:
- Deploy and configure the single Fortra (Alert Logic) agent on identified systems to enable telemetry collection and secure log transfer.
- 1.SOC Integration:
- Establish connectivity to the Fortra (Alert Logic) SOC for continuous monitoring, triage, and response.
- 1.Log Management:
- Configure secure log ingestion with a daily aggregated average limit of 100MB/node, with additional charges for exceeding storage thresholds.
Once onboarding is complete, the following activities will begin:
- Real-time detection and automated scanning for vulnerabilities, misconfigurations, and security risks.
- Continuous log ingestion and monitoring by the SOC.
- Identification, escalation, and triage of critical security events, including actionable remediation recommendations.
- Secure storage of event logs, accessible via the client portal for up to 12 months.
CLIENT PORTAL
- 1.The Detection & Response Professional service provides a Client Portal that is available 24/7/365 (excluding planned Maintenance windows).
- 2.The portal provides self-service features including fully searchable logs, access to reporting, and information to enhance the Detection & Response service experience.
ROBUST REPORTING:
- 1.Automated delivery of detailed reports that outline, rank and classify identified vulnerabilities. Detailed information is provided in the reports and via the Client Portal
BUSINESS HOURS SUPPORT:
- 1.Xamin will provide live Technical Support during Business Hours for service requests related to the Detection & Response platform. Technical support is provided for troubleshooting of the service features only.
- a.Client Submitted Requests:
- 1.Support requests can be submitted during posted Business Hours via:
- Desk Director
- Phone
- 1.An Xamin support technician will triage the Support Ticket and will provide a response based on the agreement SLA.
- 2.The support technician will troubleshoot and resolve the issue directly with the end user that requested the service.
- 1.Support requests can be submitted during posted Business Hours via:
- a.Client Submitted Requests:
- 1.If remediation of vulnerabilities or security events is desired:
- a.OPTION 1:
- i.Add additional support services to your support Agreement.
- ii.Firewall Management
- 1.Remediation of Critical and High findings related to the firewall infrastructure are included as part of the Agreement fees for Firewall Management.
- iii.Infrastructure Protection + Support
- 1.Remediation of Critical and High findings related to server, storage and network infrastructure are included as part of the Agreement fees for Infrastructure Protection + Support services.
- iv.Remediation of all Medium & Low findings are charged on an hourly basis.
- v.Remediation of all Workstation findings are charged on an hourly basis
- b.OPTION 2:
- i.Remediation services can be provided upon request on an hourly basis if no Support Agreement is in place.
- ii.Requires that Xamin is provided remote access to the affected system(s) for remediation.
- a.OPTION 1:
AFTER HOURS SUPPORT:
- 1.Critical Security Events:
- a.For Clients under a Support Agreement:
- i.Escalated Security Events:
- 1.Xamin will be notified by the SOC team for escalated Critical events.
- 2.Xamin will notify the Client via the Emergency Call Tree.
- 3.Xamin will work to troubleshoot and resolve the issue(s).
- ii.Client submitted requests:
- 1.Emergency support is only available for platform availability issues.
- 2.Requests can be submitted via Phone only to our Emergency support line.
- 3.All other requests will be addressed at the beginning of the next business day.
- i.Escalated Security Events:
- b.For Clients not under a Support Agreement:
- i.Escalated Security Events:
- 1.Client will be notified directly by the SOC team for escalated Critical events.
- ii.Client submitted requests:
- 1.Xamin does not offer emergency support for clients not under a Support Agreement.
- 2.All requests will be addressed at the beginning of the next business day and billed on an hourly basis.
- i.Escalated Security Events:
- a.For Clients under a Support Agreement:
OUT OF SCOPE OF SERVICES:
HOURLY SUPPORT:
- 1.Support for the following items will be charged on an hourly basis. Xamin will seek approval prior to commencing work.
- a.Hourly support items include, but are not limited to:
- i.Troubleshooting of security observations ranked as Informative, Low or Medium.
- ii.Requests for non-emergency work to be completed After Hours.
- iii.Customized event correlation.
- iv.Onsite Support.
- v.Hourly fees are billed in 1 minute increments.
- a.Hourly support items include, but are not limited to:
- 2.If the Client has contracted the following services in addition to Detection & Response and hardware/software is included in the Support Catalog, hourly charges may be considered in scope, covered by the Agreement and not subject to hourly charges:
- Firewall Management
- Infrastructure Protection + Support
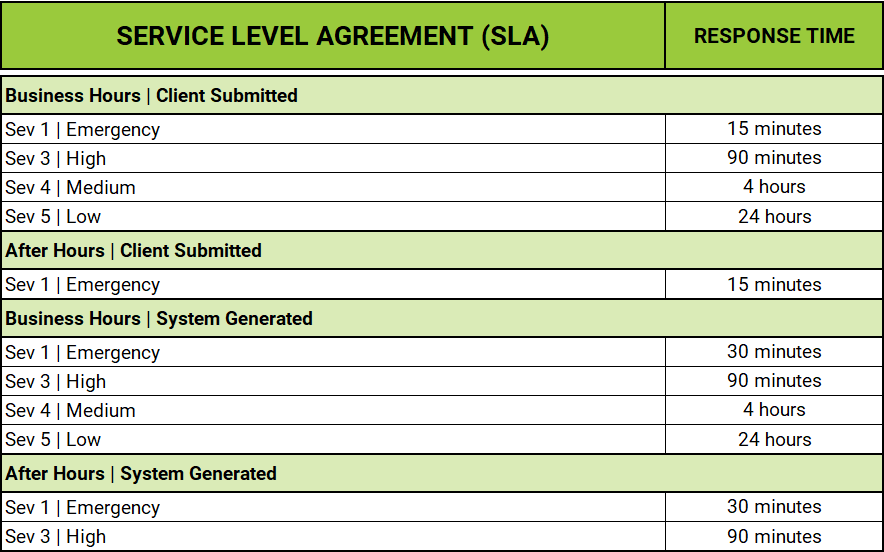
SERVICE LEVEL AGREEMENT
TECHNICAL SUPPORT HOURS:
Xamin Technical Support Hours:
- a.Business Hours: 8:00 AM – 5:00 PM CST Monday – Friday.
- b.Emergency support is provided outside of normal business hours.
- c.Holidays and office closures are determined on an annual basis and are available at: https://www.xamin.com
RESPONSE TIME